Is it possible that TikTok is a new means of cyber espionage? 3.5 billion people worldwide have downloaded the app (source), so having extensive control of devices worldwide could be a major threat.
The United States government is considering a plan to ban TikTok because of fears that the Chinese government can access the data from devices which we install the app on (source). Recent investigations have discovered that employees from TikTok have harvested data from users’ devices (source). The US government agency has already instructed individuals to wipe the app from their devices (source). Furthermore, the EU have also asked employees to remove TikTok from their work devices (source).
1.0. What is Cyber Espionage?
The European Union Agency for Cybersecurity defines cyber espionage as “the use of computer networks to gain illicit access to confidential information, typically that held by a government or other organisation” (source). Cyber espionage attacks must be covert with perpetrators aiming to conceal their identity (source). Cyber espionage is not a rare occurrence, and it is likely that many perpetrators never get discovered. Unlike cyber attacks, espionage is an unavoidable part of state affairs (source).
1.1. Aim of Cyber Espionage
The motivation surrounding Cyber Espionage can vary but it usually involves financial, political or ideological motives (source).
Threat actors aim to steal:
- Data. For example, customer details, employee numbers and financial performance.
- Information. For example, hackers may want to know about future plans that a government/organisation is planning on implementing. This may also include government trade secrets (source).
- Intellectual property. Usually involved in the business sector, hackers may want information on new product designs and inventions.
The most common targets of a cyber espionage attack are large corporations, government agencies and academic institutions (source).
2.0. Is my ‘For You’ Page Spying on me?
Is it possible that TikTok is a new means of cyber espionage? Considering the app has been downloaded 3.5 billion times worldwide (source), having extensive control devices worldwide could be a major threat. TikTok’s parent company, ByteDance, has its headquarters in Beijing. A recent investigation found that employees at the company had inappropriately obtained the data of TikTok users in the US (source).
The United States government is considering a plan to ban TikTok because of fears that the Chinese government can access the data from devices which the app is installed on (source). Already, individuals working for any US government agency have been told to wipe the app from their devices (source).Furthermore, the EU and the British government have also asked employees to remove TikTok from their work devices (source).
Media agencies are also becoming suspicious. The BBC has advised its staff to delete TikTok from any corporate phones (source). The media company cited fears that data could be harvested from business phones and shared with the Chinese government.
3.0. Methods of Cyber Espionage
3.1. Water Holing Attack
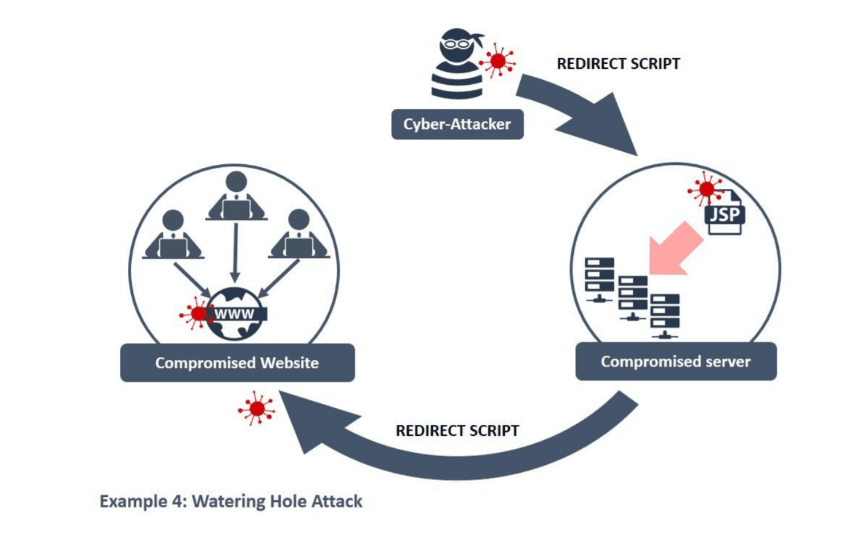
A watering hole attack, also known as supply chain attacks, involves infecting websites with an aim of accessing networks which visit the website (source). Malware can infect the systems of anyone who visits websites that have been infected. The hacker then has access to a user’s personal information, or may even take control of the computer (source). Theoretically, TikTok could be the target of a water holing attack. However, in this instance it is likely that the Chinese social media company would be a victim of an attack, rather than a perpetrator.
3.2. Spearphishing
Spearphishing is a type of cyber attack which targets specific individuals or organisations, usually through infected emails (source). One should not confuse this technique with general phishing campaigns, which are more generic and sent to a large volume of people. Spear phishing techniques involve the hacker doing research in order to make the emails more personalised and are therefore usually harder to spot as a threat. Due to the widespread nature of TikTok usage, it is unlikely that the company would use spearphishing to gain access to information.
3.3. Whaling
A whaling attack consists of a threat actor posing as a senior member of an organisation (source). The hacker will then utilise email and website access to target individual members of the organisation or reveal sensitive information. The attacker usually uses their disguise as a senior to manipulate subordinates into making wire transfers (source). To use this method, one needs a substantial level of knowledge about the targeted company. Similar to Spearphishing, the perpetrators choose targets specifically, and this method is not typically used to target a wide audience.
3.4. Advanced Persistent Threat (APT)
An APT is a sustained cyberattack in which someone remains present in a network undetected (source). We can therefore class it as Cyber espionage as it is covert. The main targets of APT are usually government networks or large enterprises (source). Experienced cybercriminals with financial support usually carry out APT assaults since they require vast resources. They select the victim networks carefully for a specific aim for these more complex attacks.
3.5. Spyware
This malware is used for the purpose of “secretly gathering data on an unsuspecting user” (source). The software allows the hacker to watch behaviour, including keyboard patterns. This then serves useful if the hacker needs information on passwords for accessing systems. This is a method that would arguably be most useful for TikTok if seeking to access foreign data.
4.0. Making a Deal with the Devil?
Data researchers found that the TikTok app carries out “excessive data harvesting” (source). For instance, when downloading the app on an android phone, it prompts the user to grant access to all phone contacts. This action has raised suspicion about why TikTok needs to collect so much information. However, others have argued that this is not a rare phenomena for social media and other mobile apps (source). Many require such information to allow better connectivity and easier access to the ‘follow friends’ feature.
However, the concerns raised by the US and the EU are not without merit. A certain Chinese law raises concerns for those using the app. The National Intelligence Law mandates that all organizations in China should be prepared to assist Chinese intelligence gathering (source). Therefore, while the data harvesting done by TikTok is likely harmless and only for business purposes, it cannot be certain that the Chinese government cannot access a user’s data.
The recent case, previously mentioned, in which employees obtained information from American users is a cause for concern (source). The parent company of TikTok, ByteDance, insisted that these employees had been fired and that they were working independently of the company. TikTok’s chief executive, Shou Zi Chew, is expected to testify before the House Energy and Commerce Committee to answer questions about links to the Chinese Government.
5.0. Other Cases of Cyber Espionage
HiatusRAT
Hiatus is a fairly new cyber espionage campaign known to be operating since June 2022. Lumen’s Black Lotus Labs released a report exposing the campaign (source). The report found that HiatusRAT allows an actor to access business-grade routers and obtain information such as emails of those accessing the router and files transferred within the network (source). The malware accessed at least 100 computers, mainly in Europe and Latin America (source).
SolarWinds
SolarWinds is a software company based in the US and it provides IT system management to thousands of organisations around the world (source). In September 2019, hackers gained access to SolarWinds network systems using malware to access system files undetected (source). ‘Nobelium’ hacked more than 18,000 public and private organisations, according to an investigation by the US Cybersecurity and Infrastructure Security Agency (source). However, it is likely that a smaller number were compromised by activity by the infiltrators. The hackers gained access to the networks of many of these organisations and would therefore have been able to obtain an abundance of data. FireEye discovered the security preach in December 2020. Otherwise, the hack would have gone undetected. The SolarWinds hacking is an example of a watering hole attack.
International Civil Aviation Organisation (ICAO)
In 2016, the UN Aviation agency based in Montreal, Canada, was victim to a case of water holing cyber espionage. Websites associated with the organisation were infected and used to spread malware to foreign government websites (source). The hackers were able to infiltrate mail servers and administrator systems, meaning the hackers gained access to more than 2000 passwords of ICAO users (source). Chinese cyber spies called Emissary Panda are the primary suspect in this case (source). This group has ties with the Chinese government according to a report by cybersecurity firm SecureWorks (source).
6.0. Conclusion
As previously discussed, cyber espionage is a method in which hackers can gain access to data and information from competitors whether it be states or businesses. Is this something we should be worried about? Cyber espionage is a growing threat in the current era of globalisation. Cyber espionage cases make up approximately 20% of data breaches worldwide (source). There are steps organisations can take to avoid being impacted by cyber espionage. Using a VPN-based access to networks holding sensitive information can allow organisations to avoid some attacks (source). Patch management software can also allow businesses to decrease any vulnerabilities in network systems (source). When it comes to social media, however, the likelihood is that government organisations will continue to ban the app from staff devices to remain protected from any possibility that Chinese intelligence services may access the data.

