
Key Judgments
Operation DisrupTor is the latest in a string of operations targeting the dark web illicit trade marketplaces. Managing to secure over 500KG of illegal drugs, it has likely destabilised the drug trade online in the short-term. Despite the increase in activity online, it is almost certain that the most effective tactics for law enforcement remain a mix of online technology and continued use of traditional techniques. The weak links among the drug trade on the dark web continue to be the logistics, such as shipping. Encrypted Messaging services, such as Telegram, will almost certainly remain an additional resource for dark web marketplaces, rather than replacing them.
Operation DisrupTor: “The golden age of dark web marketplace is over” – Europol

On the 22nd of September 2020, a partnership of law enforcement organisations across the world collaborated to execute Operation DisrupTor, named after The Onion Router (TOR) network. With agencies from nine countries including the FBI, Germanies Bundeskriminalamt (Federal Criminal Police Office, FCPO) and the United Kingdom’s National Crime Agency (NCA), 179 arrests were made in total.
There were over 500kg of drugs that were confiscated, consisting of:
- Fentanyl
- Oxycodone
- Hydrocodone
- Methamphetamine
- Heroin
- Cocaine
- Ecstasy
- MDMA
- Collection of other addictive medicines
Along with this, $6.5 million in cash was seized along with 64 firearms. One hundred twenty-one arrests were made in the United States, 42 in German, 8 in the Netherlands, 4 in the United Kingdom, 3 in Austria and 1 in Sweden.
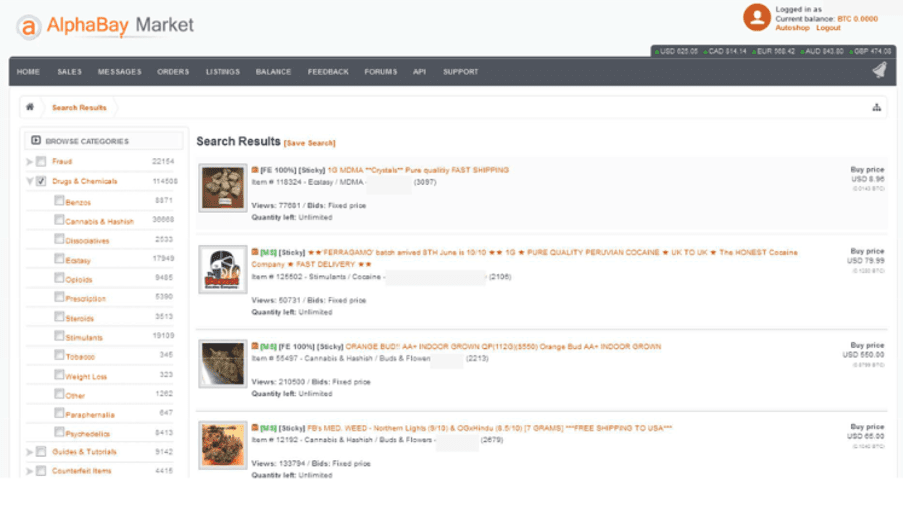
Operation DisrupTor targeted suspected criminals that had been using dark web marketplaces such as Alphabay and Dream (which had been shut down in a separate United States operation in 2019). Although the dark web has been used to write sensationalist headlines in tabloids, it is still a rather small marketplace. Of the 55,828 onion domains (a website only accessible via the TOR network) Recorded Future explored in 2019, only 8,416 were found to be live (15.1%).
The Dark Web markets
DisrupTor is as a continuation of legal action against dark web marketplaces. On the 3rd of May 2019, Europol disclosed that they had taken down two other well-known marketplaces, Silkkitie (referred to as the Valhalla Market) and Wall Street Market. The FCPO shut down the Wall Street Market, while Tulli (Finish Customs) were able to shut down Valhalla. These sites were hotbeds for selling narcotics among other illicit goods. Over 1,150,000 customer accounts were found registered on the Wall Street Market.
The dark web has grown to be one of the most popular sources to obtain illicit drugs. The European Drug Report 2020 found that, after trusted suppliers, the dark web was the second most popular means to source MDMA, and at worst the fifth most popular source of narcotics included in the report.
Law Enforcement Techniques
To combat these marketplaces, law enforcement can either take a technology focussed route (which is fraught with legal hurdles when it comes to jurisdiction) or more traditional investigative means. The FBI used a Flash-based app called Metasploit Decloaking Engine (or more informally The NIT) to reveal IP addresses despite encryptions and proxies. Placed on three servers that investigators had found in connection with Child Pornography, the FBI bated users into using the server and discovered their IP addresses. It was later found to be reliable in court.
The TOR network runs through at minimum three relays, anonymising end-user information. Middle Relays are open to the TOR network, and users can connect to these. However, IP information in these relays will not show as the source. The exit relay is the final point of call before the final destination, and this IP address is interpreted by the network as the source IP address.
TOR is also vulnerable to various other intrusions, such as confirmation attacks. On the 4th of July 2014 workers for TOR found relays that were assumed to be trying to identify network users using this technique. Running from the 30th of January 2014 until it was found on the 4th of July, they found 115 infected relays on the network (6.4% of the whole system). ATagging attack, another form of a Confirmation attack, is when malicious forces control the entry relay and exit relays. If they have control of the entry and exit relays, they can detect and alterations that have been made in the middle relays and can confirm identities.
Despite these techniques to find hidden identities, given the worldwide nature of the users, traditional law enforcement tactics are still necessary for combating this threat.
With Operation DisrupTor being the combination of separate operations being co-ordinated through Europol, it showcases the need for global law enforcement co-operation. Having a platform such as Europol as the central hub with individual police forces as the spokes in the combat against dark web illicit trade will be crucial in the use of traditional police techniques.
The weakest links in the dark web trade are still the logistical means of supply in the physical world. Undercover operations and observation are still needed, despite the fight against a seemingly faceless online operation. Law enforcement agencies are still using these techniques, and will almost certainly continue to use them along with growing tech powers.
The burgeoning use of Encrypted Communications: With the clampdown on the dark web markets, there has been a trend of gangs and organisations to shift towards encrypted messaging apps such as Telegram. An anonymous source who works as a dark web researcher told The Independent.
“Telegram has become the tool of choice for criminals, but it is not the first app to be put to nefarious use. Channels such as WhatsApp and Facebook Messenger had their day in the criminal underworld too, so Telegram will likely not be the last.”
With a much easier entry than dark web marketplaces (having only to download apps such as Telegram from an app store on a smartphone), these new services likely present sellers with a wider market. The names of each channel are easier to spread in the public, with graffitied hashtags seen near mass transport hubs. Along with easier advertising, sellers are using chatbots to facilitate any deals to deny culpability.
Yet, despite the supposed anonymity of encrypted messaging, it is unlikely that we will see a shift from the dark web to solely encrypted messaging services. A big challenge facing suppliers will almost certainly be the marketing of any goods and services on a messaging app. Most messaging apps are small in scale in comparison to the dark web and are limited in terms of geography.
Despite apps like Telegram having channels for mass encrypted communication, the User Interface is almost certainly not giving vendors the same footfall as they once had. With one channel offering drugs, another may provide firearms, instead of all products being on one marketplace, reducing the profit potential of any organisation running a channel.
These limits will likely lead to the adoption of apps such as Telegram to run adjacent to dark web marketplaces. Although easier to access and still able to move quickly upon detection in the ability to set up a new channel, security and profit concerns are still key sticking points. It will likely be difficult for encrypted messaging to make dark web marketplaces obsolete.
What’s Next?
Governments are fighting to have greater access to encrypted devices, posing a realistic possibility of hindering the growth of the dark web should laws be passed. In the United States, Republican lawmakers introduced a bill (H.R. 7891) in June 2020 that would force companies to decrypt any data should a warrant be issued for communications.
It is highly likely that COVID-19 has increased the activity within online markets on the dark web. With a reduction in person to person contact with social distancing and governmental orders, marketplaces on the dark web, encrypted messaging services and social media, in general, are appearing to be playing a larger role in the distribution of narcotics.
The takedowns of the markets that we see in operations such as DisrupTor also seem only to have a short-term impact, likely adding fuel to this turn towards digital drug sales. The biggest effects recorded after the takedowns of markets such as the original Silk Road have been an increase in price for illegal goods for a limited time, and a fall in the value of bitcoin.
Conclusion
While Europol has declared that the ‘Golden Age’ of the dark web is over, it has proven highly resilient to previous attacks. Operation DisrupTor is only the latest in a chain of operations to counter the illicit online trade, and future operations will almost certainly still rely on ‘old school’ methods of prevention, rather than solely on new technology. Encrypted messaging is almost certainly serving as an extension of the dark web marketplaces, rather than replacing them entirely. With this, it is highly likely there will come renewed pushes by governments to enact further surveillance measures to gain backdoor access after the COVID-19 pandemic has subsided.
Image 1: FBI / Twitter (link)
Image 2: Rand (link)
Image 3: FBI / Youtube (link)
Image 4: Screen Capture of Bank Info Security (link)

